The risk-based approach in Anti-Money Laundering Compliance
The risk-based approach in Anti-Money Laundering Compliance
The principal AML regulation in Singapore, viz., Corruption, Drug Trafficking and Other Serious Crimes (Confiscation of Benefits) Act 1992 and various guidelines issued by the Monetary Authority of Singapore (MAS) require regulated entities to adopt a risk-based approach in Anti-Money Laundering Compliance.
With the revised FATF International Standards on Combating Money Laundering and the Financing of Terrorism and Proliferation, issued in 2012, the risk-based approach has become central to fulfilling various requirements set therein.
The FATF requires applying a risk-based approach at several levels, starting at the country level in the form of national ML/TF risk assessment, then at the state, and finally at the company level.
History of risk-based approach:
Earlier, financial institutions, banks, and other non-financial businesses and professions followed the regulatory requirements concerning customer risk assessment.
It was a tickbox kind of approach where every customer and the regulated entity were treated equally irrespective of their risk appetite and the risk carried by them. The companies used to follow a checklist and collect documents required by the law to comply with the risk assessment requirements.
Many criticized the one-size-fits-all approach as each entity is different in terms of its business, customers, products, services, and related risks. This led to adopting the risk-based approach in dealing with financial crimes like anti-money laundering.
What is the principle of risk-based approach (RBA)?
In simple terms, the risk-based approach refers to adopting a methodology where risks are identified, assessed, and managed in accordance with the amount of damage they can cause. The risk-based approach follows the principle of “higher the risk, higher the amount of controls.
The firms resort to the risk-based approach as the resources are always scarce, and they must be deployed in such a way that they can be optimally utilized.
What is the risk-based approach in anti-money laundering?
Financial Institutions, Non-Financial Businesses and Professions, and Virtual Asset Service providers are the primary targets of financial criminals. There are a variety of financial crime risks, and these risks are associated with products, services, customers, geographies, delivery channels, technology, and more.

Companies need to combat money laundering risks in such a way that resources are optimally utilized. The risk-based approach in anti-money laundering enables companies to prioritize the risks in order of their impact and then apply suitable measures proportional to the level of risks posed by customers, products, services, geography, and delivery channels.
What is the need for a risk-based approach in anti-money laundering?
Each company is different in terms of products and services, customer base, delivery channels, geography, technology, and more; hence, a one-size-fits-all approach in terms of deploying controls to counter money laundering risks can not work.
The companies should be able to assess their own money laundering and terrorist financing risks and take necessary measures to counter them, and there comes the need for the adoption of a risk-based approach.
The adoption of a risk-based approach forces companies to understand various ML/TF risks they are exposed to and tailor their AML/CFT program to counter them.
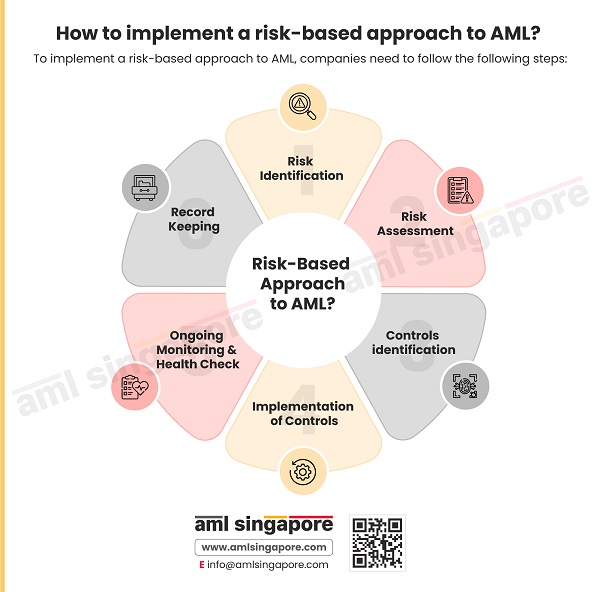
How to implement a risk-based approach to AML?
1. Risk Identification
2. Risk Assessment
Each risk needs to be assessed in terms of its likelihood and potential impact on the business. Normally, risk factors are assessed in terms of their impact, viz., low, medium, and high.
3. Controls identification
4. Implementation of Controls
5. Ongoing Monitoring & Health Check
6. Record Keeping
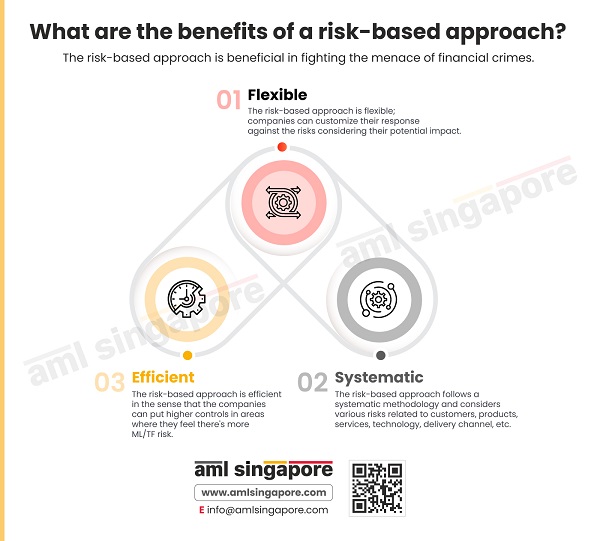
What are the benefits of a risk-based approach?
The risk-based approach is beneficial in fighting the menace of financial crimes.
1. Flexible
The risk-based approach is flexible; companies can customize their response against the risks considering their potential impact.
2. Efficient
The risk-based approach is efficient in the sense that the companies can put higher controls in areas where they feel there’s more ML/TF risk.
3. Systematic
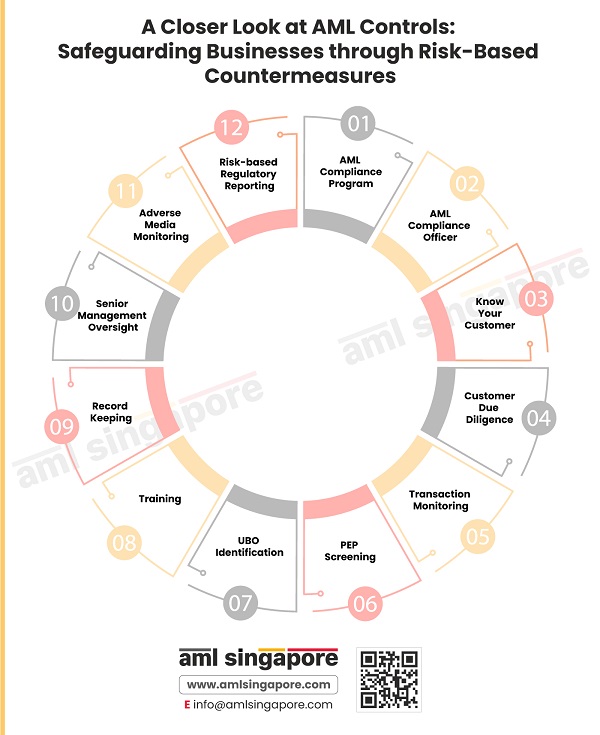
What controls are commonly employed by companies adopting the risk-based approach to counter ML/TF risks
- AML compliance program: It is best to have an effective AML compliance program that consists of AML policies, procedures, and controls. The business must create an AML policy document in line with its ML/TF risk. The AML compliance program is then implemented to counter various money laundering risks.
- AML compliance officer: The AML compliance officer is responsible for implementing the AML framework approved by the board of directors. He ensures that the AML/CFT policies and procedures are followed regularly and that the staff is adequately trained to counter money laundering and terrorist financing.
- KYC: Know Your Customer (KYC) is an integral part of the onboarding process in which the business collects customer documents to verify their identity. The business must know whom they are dealing with and understand the risk associated with the customer profile.
- CDD: Customer Due Diligence (CDD) is a significant part of an AML compliance program. The compliance department verifies various documents and performs screening, in-depth investigation, and customer risk assessment. A decision to onboard the customer is made based on the customer acceptance policy. In the case of high-risk customers, Enhanced Due Diligence (EDD) is performed, and the source of funds, source of wealth, and top management approval is obtained before entering into a business relationship.
- Transaction monitoring: A business must closely monitor the transactions and detect any suspicious activity. With continuous monitoring, the business can identify and prevent money laundering attempts immediately. It can file suspicious transactions with the authorities and diligently follow the AML rules and regulations. Transaction monitoring lets the business keep track of customer behavior and detect unusual patterns that might be connected to money laundering.
- PEP Screening: PEP refers to Politically Exposed Persons. They hold influential positions or have political connections to help them gain an undue advantage. Such a customer profile is highly risky because of access to funds and power. So businesses must carry out EDD – Enhanced Due Diligence process, monitor transactions and report suspicious activity as part of a proactive AML compliance program for PEPs.
- UBO Identification: Identifying the Ultimate beneficiary ownership is a part of the risk-based approach that a business must integrate to know the ultimate beneficiary of the transactions. UBO identification lets the company correctly understand the real beneficiary behind the legal structures and take appropriate measures to counter money laundering risks.
- Training: Regular training helps frontline staff know emerging risks and associated red flags they can apply while dealing with customers. A refresher training for the compliance department will help institute a common understanding of AML/CFT policies and procedures. Further, training the top management will help secure their commitment to the AML/CFT efforts put in by the business.
- Record Keeping: The company must document and maintain the Enterprise Wide Risk Assessment (EWRA) performed by it. Various risk factors, their likelihood, and their impact, must be documented along with the controls put into effect by the company. The risk appetite of the company and the residual risk must be documented so that the necessary corrective measures can be recommended by the compliance officer and approved by the top management.
- Senior management oversight: The senior management must be aware of the company’s ML/TF risks exposure to formulate strategies to mitigate and manage the risks. The board must approve and oversee the implementation of the AML/CFT program and ensure that it aligns with the company’s risk-based approach. Further, senior management must approve all high-risk customers before entering into a business transaction with them.
- Adverse Media Monitoring: Adverse Media Monitoring helps understand negative media reports against a customer or a potential customer. It helps the compliance officer understand if the customer has a criminal history. Criminals generate dirty money by committing predicate offenses, then try to place that money into the legitimate economy. Adverse media monitoring helps identify risks associated with a customer and take the necessary measures to counter ML/TF risks.
- Risk-based regulatory reporting: A business can prevent money laundering and financing of terrorism by reporting suspicious transactions. Continuous transaction monitoring helps in identifying unusual customer behavior and preventing crime. All suspicious activities and transactions must be reported to Singapore’s Suspicious Transaction Reporting Office (STRO). It is a risk-based approach that helps companies protect their organization against reputational damage, helps to safeguard customers’ interests and abide by AML rules and regulations.
Risk-based approach examples
Example 1:
An accountant deals with a customer hailing from a country known for weak AML laws.
To mitigate and manage this risk, the compliance team requests for AML/CFT policy of the customer, classifies the customer as high-risk, and conducts Enhanced Due Diligence.
Example 2:
A financial institution identifies a sudden increase in cash deposits by a customer.
To mitigate and manage this risk, the compliance team requests fresh KYC documents to understand if there is a change in the business activities of the customer, asks for the source of funds, carries out ongoing monitoring, and evaluates whether to offboard the customer in accordance with the customer exit policy and file suspicious transactions report.
How often should the risk assessment be carried out under the risk-based approach?
As a best practice, the risk assessment should happen at least once a year. However, new product introduction, identification of new risks, and changes in national risk assessment could trigger a fresh ML/TF risk assessment.
How should AML/CFT program take account of the risk-based approach?
The AML/CFT program should be drafted in line with the Enterprise-Wide Risk Assessment performed by the regulated entity. The risk factors having the greatest impact must be adequately managed and controlled. Various risk factors like products, services, customers, geography, technology, and delivery channels must be considered while defining procedures around customer risk assessment. Further, the customer acceptance policy should define customer onboarding criteria and procedures. Red flags concerning the business must be documented, and the staff must be trained to identify and tackle them. Written procedures must be drafted to report all suspicious activities and transactions. The AML/CFT program must document criteria and procedures around the ongoing monitoring of a business relationship. Further, the requirements around Enhanced Due Diligence must be documented to counter the risks arising from a high-risk customer. Sanctions screening requirements should be clearly documented and explained to the staff.
Risk-based approach with Sanctions Screening Software
The sanctions screening software helps identify if the customer is a sanctioned individual or entity. Its underlying database must be updated regularly to counter the new risks arising out of newly listed individuals and corporates. Further, it must be configured in such a way that false matches are reduced, and true matches are identified and escalated immediately.
Risk-based approach with transaction monitoring software
The transaction monitoring software must be configured in such a way that red flags concerning customers are given due consideration while processing the transactions. The entity must be able to define rules and scenarios requiring the immediate attention of the compliance team. All suspicious transactions must be automatically flagged for further scrutiny and action by the compliance department.
Why adopt a risk-based approach?
The global best practices in countering ML/TF advocate adopting a risk-based approach. The risk-based approach aims to follow the legislation’s true intent and prevent financial crimes. It’s a systematic approach providing flexibility to an entity to implement necessary controls to counter ML/TF risks. The risk-based approach is more efficient in countering money laundering and terrorist financing. Further, it minimizes the cost of compliance and undue hardship on customers. It is dynamic enough to respond to new and emerging risks in line with the changes in ML/TF typologies.
Adopting a risk-based approach to AML/CFT
It is best to have a risk-based approach to prevent money laundering and financing of terrorism. Companies should create an AML compliance program in which KYC is a critical part. The Know Your Customer policy lets the business know who the customer is and whom they will onboard. It helps in risk assessment and mitigation with the appropriate measures. KYC and CDD are the foundation of an AML program, and so businesses must follow the rules and regulations to avoid non-compliance and legal consequences such as penalties. A business should also invest time in sanction screening to find if a customer is on the sanction list and make informed decisions to continue or discontinue the business relationship. Other elements in the risk-based approach are PEP- Politically Exposed Persons, and UBO- Ultimate Beneficiary Ownership.
Adopt a risk-based approach with an AML consultant
Financial institutions need to implement a program with a foundation laid on a risk-based approach. If you are looking for the best AML consultants to help you adopt a risk-based approach and combat money laundering and financing terrorism, AML Singapore can meet your requirements. We offer a comprehensive range of services such as AML Policy Documentation, AML Business Risk Assessment, AML Training, In-house AML compliance Department set–up, AML Software selection, and other services.

About the Author
Pathik Shah
FCA, CAMS, CISA, CS, DISA (ICAI), FAFP (ICAI)
Pathik is a Chartered Accountant with more than 26 years of experience in governance, risk, and compliance. He helps companies with end-to-end AML compliance services, from conducting Enterprise- Wide Risk Assessments to implementing the robust AML Compliance framework. He has played a pivotal role as a functional expert in developing and implementing RegTech solutions for streamlined compliance.