Step-by-Step Process: Executing a Comprehensive Transaction Monitoring Program
Step-by-Step Process: Executing a Comprehensive Transaction Monitoring Program
Transaction Monitoring is a crucial element of the AML compliance program, focusing on continuously tracking customer activities to detect any suspicious pattern or unusually large value transactions.
The success of the transaction monitoring program is highly dependent on how systematically the same has been implemented. Let us discuss this step-to-step process of executing a robust and effective transaction monitoring system:
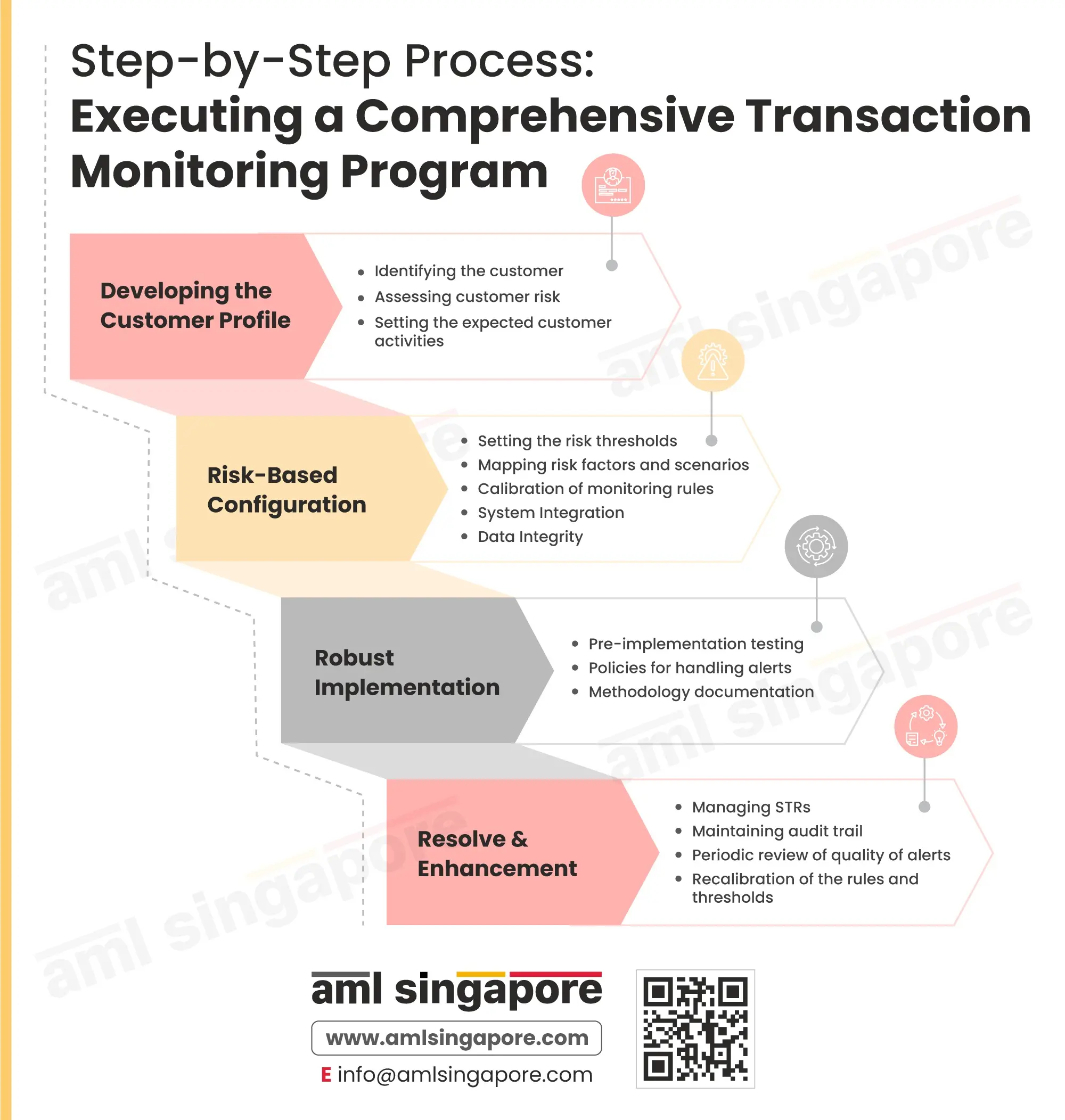
- Developing the Customer Profile:
The customer’s profile would serve as a base against which the monitoring rules shall be applied. Thus, the primary step for implementing the AML transaction monitoring function is identifying the customer and assessing the expected risk associated with such a business relationship. The regulated entity must also determine the normal or expected customer activities, considering the identification details and risk profile. - Risk-Based configuration:
Now, the entity must define the potential risk scenarios associated with the assessed exposure. Further, the entity must also develop and configure the monitoring rules and thresholds, building upon the customer’s profile. During this phase, the data integrity and the system integration must be checked to ensure data accuracy and completeness, which will be used for monitoring. - Robust Implementation:
To ensure the efficient working of the defined monitoring rules and parameters, it is essential that the regulated entity conducts adequate testing and addresses the identified bugs immediately. Further, the systems must be backed by comprehensive documentation around handling the alerts triggered by the systems and the overall methodology for monitoring the transactions. - Resolve and Enhancement:
The entity must appropriately manage the disposition of the alerts and filing of the Suspicious Transaction Reports (STRs). A complete transaction audit trail must be retained, along with the alerts generated and its management.
Further, to enhance the quality and effectiveness of the transaction monitoring system, the entity must periodically review the systems to determine the quality of the outcome, the number of false positive triggers, etc. Wherever required, the mapped logic and monitoring thresholds must be revamped and recalibrated to ensure no suspicion goes undetected.
Here is an infographic discussing the stepwise process for implementing a comprehensive transaction monitoring program and reinforcing the AML efforts.
If you need assistance establishing an AML function, including the tools and systems, here we are – AML Singapore, offering end-to-end AML support for your AML compliance obligations.